Dedaub Watchdog and Contract Library launch on Fantom

We are thrilled to announce that we have collaborated with Dedaub to launch the Watchdog continuous smart auditing system and the Contract Library smart contract explorer on Fantom.
Smart contract vulnerabilities remain a pressing problem across the crypto industry. In Q1 2022 alone, hackers stole $1.3 billion in cryptocurrencies; 97% of these exploits focused on DeFi products.
Crypto protocols conventionally rely on third-party, manual audits to uncover security flaws. While an irreplaceable industry standard, manual audits can be costly and time-consuming. Moreover, new threats can arise as protocols evolve, and a completed audit can quickly become outdated.
Dedaub’s groundbreaking solutions supplement manual audits with automated vulnerability detection services that are continuously updated to address newly discovered exploits.
What is Contract Library?
Contract Library is a free contract-centered blockchain explorer available to all. First released in 2018, Contract Library continuously decompiles and analyzes all deployed contracts for human inspection and offers a platform for exposing vulnerabilities. Contracts added to the Fantom network appear in the library almost immediately.
Contract library can:
- Examine contract code at all levels, including bytecode, decompiled representations, and source code, if available.
- Check token balances and allowances ‒ both as grantor and grantee ‒ for every contract and account.
- Read the values of storage locations of a contract.
- Interact with a contract (“read/write contract”), even if it has no published source code.
- Find identical contracts, as well as similar public functions.
- Decompile arbitrary bytecode ‒ for instance, to examine attack contracts or to see if high-level code is translated into gas-efficient sequences.
- Examine transaction traces and effects, filter past actions by function, and perform local debugging of transactions.
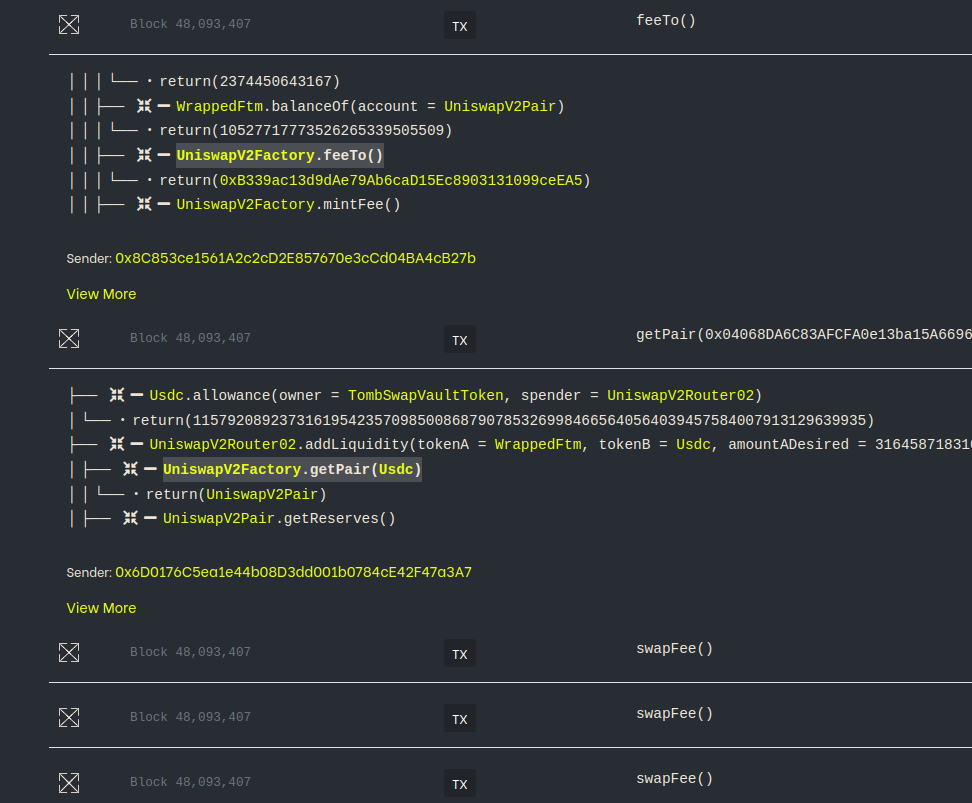
Contract Library’s debugger is orders of magnitude more scalable than alternatives on other networks, enabling debugging complex transactions within a reasonable amount of time. This is achieved by implementing an efficient model of the EVM to offload computation from the Web3 client.
What is Watchdog?
Dedaub’s flagship product is built on Contract Library. Watchdog is an automated, continuous auditing system that analyzes selected smart contracts from the Fantom Network. Any flagged warning is examined by a human auditor and escalated if judged to be valid and high-value.
Used by the industry’s leading DeFi protocols, Watchdog:
- Runs 24/7 and performs analysis for over 80+ different types of exploits, including some of the most subtle exploits that involve contract-to-contract interactions.
- Periodically updates and improves with new attack vectors as new research emerges.
- Dynamically updates with the latest network data and smart contracts of selected projects, including information about
- Total Value Locked (TVL)
- Contract approvals
- Pool sizes
- Proxy configurations
- Whether an address has special privileges
- Continuously updates each monitored project’s state, using insights gained in conjunction with static analyses to reduce false positives and prioritize inspections.
- Automatically escalates warnings to a Dedaub expert inspector capable of efficiently addressing an issue and notifying the relevant project team.

Combining automated monitoring with real-time alerts, Watchdog works to discover vulnerabilities in smart contract systems before hackers can exploit them.

How can projects access Watchdog?
DeFi projects with at least $10 million in TVL and selected NFT-related projects will automatically have their smart contracts read into the Watchdog system.
Each project will receive administrative access to see a list of vulnerabilities within their smart contracts at any time. Projects can manually query each smart contract against any exploit recognized by Watchdog.
Periodically, an expert auditor from Dedaub will review each smart contract. If a vulnerability is detected, Dedaub will notify the project team, assist them in analyzing related risks and dangers, and support the project in fixing the vulnerability.
Watchdog issues cumulative PDF reports summarizing issues and inspections performed.
If you would like to add your project to Watchdog, email watchdog@fantom.foundation with the following information:
- Project Name
- Smart contract addresses on-chain
- Telegram IDs or e-mail addresses to give admin access to.
- Proof that you are the developer/owner of the smart contracts, such as: signing a message with the admin key(s) of the smart contract or signing a message with the EOA that deployed the smart contracts.
Vulnerabilities
As of 28 October 2022, this is a list of vulnerabilities that Watchdog can analyze:
[The same vulnerability could have multiple analyses, at different confidence levels, or variants.]
- Accessible selfdestructSELFDESTRUCT target address can be overwritten by untrusted external caller
- Arithmetic errorArithmetic overflow or underflow can occur due to unchecked operations
- Bad RandomnessBad source of randomness can be exploited by untrusted caller
- Call and Delegate Together Contract may call same target address with both a regular call and a DELEGATECALL
- Call DoS (Denial-of-Service) An external call to an untrusted contract can block important further functionality
- Call to Tainted FunctionA call that can be reached by untrusted users allows calling any function on behalf of the contract
- DoS (Denial-of-Service) through iteration/external operation/ether transfer An untrusted user can hinder further operation of key contract functionality
- ECDSA without chainIdECDSA signed data do not include the chain id and can be replayed in other networks
- ECDSA signature malleability ECDSA signature used as key to data structure, a twin, equivalent signature can be produced by an attacker but would not map to the same data
- ERC20 UnderflowUnderflow of the balances array found in ERC20
- Flashloan unchecked callback The callback function of a flash loan (for DyDx, Aave, Uniswap v2, and more) does not check who initiated the flash loan
- Inconsistent assertionsSensitive operation can be reached by different entry points without the same assertions being made consistently
- Inconsistent call arg scalingArguments of external calls to the same function are scaled using different decimal constant factors (e.g., 10^8 vs 10^18)
- Inconsistent ECDSA signingECDSA signing includes several arguments of a function but skips one or more.
- Inconsistent storage scalingDifferent writes to the same storage field are scaled using different decimal constant factors (e.g., 10^8 vs 10^18).
- Looped delegateCall and msg.value DELEGATECALL operations used in a loop to unknown function, without checking the caller, and with “msg.value”
- No-op external function callExternal view/pure call has an unused result.
- No-op internal function callInternal call with no side effects has an unused result
- Permit omits sensitive variablePermit call does not sign sensitive variable
- Reachable assertSpecific values found that cause low-level assert to fail. Such an assert should only be emitted by the compiler for safety and is not expected to fail for valid values
- ReentrancyExternal call operation to user-controlled address possibly susceptible to reentrancy attack
- Repeated CallsRepeated external calls to contract controlled by untrusted caller can allow them to return inconsistent results.
- Sensitive call can be reached by anyoneSensitive call to DeFi API can be reached by untrusted external caller
- SSTORE to tainted addressSSTORE operation writes to a tainted, user-controlled storage address. Should only happen via assembly
- Stale value in storage|The contract seems to be caching volatile values, derived over the storage variables of another contract
- Suspicious money burn operationSuspicious call to sensitive money burn operation
- Suspicious money transfer operationSuspicious call to sensitive money transfer operation.
- Suspicious revert inside loop An untrusted user can supply values that cause a loop to revert, preventing other iterations
- Swap publicly reachableSwap operation can be reachable by untrusted external caller
- Tainted DELEGATECALL Target address of DELEGATECALL operation can be controlled by untrusted caller.
- Tainted ERC20 Token TransferVarious parameters (target token, fund receipt) of an ERC20 token transfer call can be controlled by an untrusted external caller
- Tainted Ether ValueETH send operation has target and value that can be controlled by untrusted caller
- Tainted money-sensitive var in external call Untrusted callers can control the value of a sensitive argument of an external call
- Tainted Ownership GuardStorage field used in guarding logic can be overwritten by untrusted caller, allowing them to bypass sensitive guards.
- Tainted Owner Variable Storage field used in guarding logic can be overwritten by untrusted caller, allowing them to bypass sensitive guards
- Tainted selfdestruct SELFDESTRUCT target address can be overwritten by untrusted external caller
- this.call() Contract makes external call to itself, whose only purpose would be to change "msg.sender"
- transferFrom proxy A public function may call transferFrom for arbitrary addresses
- Transfer of entire balanceA token transfer sends the entire balance of the contract, so that an untrusted user can artificially inflate their balance (by token transfers and not normal interaction with the contract) while always getting the extra amount back
- Transitive ReentrancyExternal call to known protocol can cause reentrancy
- Uniswap-like price manipulationA swap on Uniswap/Sushiswap/similar clone can be price-manipulated
- Uniswap-like tainted tokenA swap on Uniswap/Sushiswap/similar clone can be made for untrusted token
- Unrestricted approve proxy The contract can be manipulated to give token approvals to untrusted parties
About Dedaub
Dedaub combines significant security expertise with cutting-edge program analysis technology to secure your projects. Our technology offers most of the practical advantages of formal verification at a fraction of the human effort, enabling thorough one-time or continual security audits. Dedaub is recognized as a key provider of Web3 security solutions and works with many of the world’s leading protocols.
Web | Media | Telegram | Twitter | GitHub
About Fantom
Fantom is a fast, scalable, and secure layer-1 EVM-compatible platform built on a permissionless aBFT consensus protocol. On Fantom, transactions are confirmed in one second and cost about one cent. Speed, low transaction costs, and high throughput make Fantom ideal for DeFi applications and real-world use cases.
Website | Docs | Research papers | Discord | Telegram | Blog | Twitter | Reddit | Github